Over the last decade, genomics has moved from research-only environments into clinical workflows, and the digital infrastructure supporting that shift has struggled to keep up. The NIH has repeatedly highlighted the exponential growth of sequencing output, and the U.S. Office of the National Coordinator for Health IT (ONC) continues to emphasize that genomic results must be handled with the same rigor as any HIPAA-regulated clinical data. Meanwhile, the CDC notes that genomic data, because of its inherent identifiability, carries unique privacy risks not present in traditional lab data.
Yet in our work across genomics companies, health systems, and precision medicine programs, one pattern stands out:
Most teams underestimate what it truly means to build a HIPAA-ready genomics platform.
They underestimate the architectural implications, the data-layer controls, the cross-system dependencies, the cloud posture required, and the operational guardrails needed to maintain compliance as pipelines scale.
This article is written for leaders evaluating vendors, choosing internal architectures, or planning modernization: Directors and VPs of Genomics, Bioinformatics leads, LIMS managers, CTOs, CIOs, Digital Health founders, and precision medicine teams who need a clear, technically rigorous roadmap.
By the end, you'll have a complete framework for developing (or buying) a HIPAA-aligned genomics platform supported by architecture patterns, compliance considerations, common mistakes, and implementation best practices rooted in real-world workflows.
Why HIPAA for Genomics Is More Complex Than Most Teams Expect
Genomic data is different.
Unlike standard clinical attributes, age, diagnosis codes, and labs, DNA data is intrinsically identifiable. Even pseudonymized VCF files can be reidentified with moderate computational effort when cross-referenced with public genomic datasets. This reality drives stricter interpretations of the HIPAA Security Rule for genomics-heavy platforms.
Common triggers that increase security scope include:
- Whole Genome Sequencing (WGS) or Whole Exome Sequencing (WES) output
- Long-term archival of FASTQ/CRAM files
- AI/ML model training on genomic + clinical combined datasets
- Cross-entity data exchange (LIMS ↔ EHR, LIMS ↔ CRO, cloud ↔ on-prem)
- Automated variant interpretation pipelines
- Patient-facing genomics reports or portals
HIPAA compliance here isn't just encryption or audit logs; it fundamentally shapes architecture, workflows, and lifecycle operations.
Yet many teams enter platform development assuming HIPAA is just a checkbox, only to realize late in the build that their cloud, ETL, data lineage, or pipeline orchestration choices create compliance gaps that require a redesign.
The Problem: Most Genomics Teams Don’t See the Compliance Risk Until It’s Too Late
In our experience, HIPAA issues emerge from three root causes:
1. Research-first engineering culture
Bioinformatics teams often prototype pipelines in a research mode, flexible, fast, Unix-centric, S3-oriented, then attempt to productionize them.
Typical problems:
- No structured audit trail for pipeline steps
- Manual data movement
- Pipeline containers built without controlled dependency management
- Lack of role separation between dev, bioinformatics, and ops
- No PHI-safe logging or redaction pipeline
This creates security gaps that are extremely expensive to remediate post-launch.
2. Underestimating the breadth of HIPAA technical safeguards
HIPAA's vague language leads to dangerous assumptions. Executives often assume:
As long as AWS/GCP/Azure are HIPAA eligible, we're compliant.
Not true.
Being cloud-eligible only means you can build a compliant system on it. It does not guarantee your VPC, access policies, pipelines, or logs meet requirements.
Teams often overlook:
- Cross-account IAM strategy
- Secure processing zones for PHI
- Encryption key segregation
- Minimum-necessary data exposure in pipelines
- Logs that accidentally capture sample IDs or metadata
- PHI inside workflow orchestration systems
3. EHR interoperability increases the attack surface
Many platforms are maturing toward EHR connectivity:
- HL7 v2 messages
- FHIR-based genomic reports
- Genomics ordering workflows
- CDS (Clinical Decision Support) hooks
But adding EHR connectivity introduces:
- Strict authentication/authorization requirements
- Mandatory auditability
- New breach-reporting obligations
- New PHI flows across internal and external systems
Teams commonly fail to build an architecture that isolates EHR-connected subsystems from internal research pipelines.
Industry Benchmarks: What Mature, HIPAA-Aligned Genomics Platforms Look Like
From our work across genomics labs, digital health companies, and precision medicine programs, high-performing platforms share characteristics:
Data handling
- Tiered storage architecture (hot/warm/cold) with retention policies
- Automated deletion and archival workflows
- Versioned, immutable pipeline outputs
- Strict PHI-free analytical datasets for R&D
Access control
- Fine-grained RBAC based on job function
- Segregated developer/non-developer access to production data
- Strong policies for bastion hosts/jump boxes
- No personal access keys in CI/CD workflows
Cloud security
- Private VPC with restricted egress
- Boundary-limited subnets for PHI processing
- Controlled metadata endpoints
- Customer-managed encryption keys
Pipeline orchestration
- Fully auditable workflow execution environment
- Reproducible container builds
- Metadata tracking at each pipeline stage
- PHI-free logs
Operational maturity
- Documented incident response playbooks
- Quarterly access reviews
- Monitoring for anomalous data movement
- Vendor risk management
These benchmarks form the foundation for the implementation guide below.
Step-by-Step Implementation Guide: Building a HIPAA-Ready Genomics Platform
Below is the implementation blueprint NonStop typically uses with genomics clients.
Step 1: Define the Data Classification Model
HIPAA-sensitive data in genomics varies across workflows.
Recommended classification
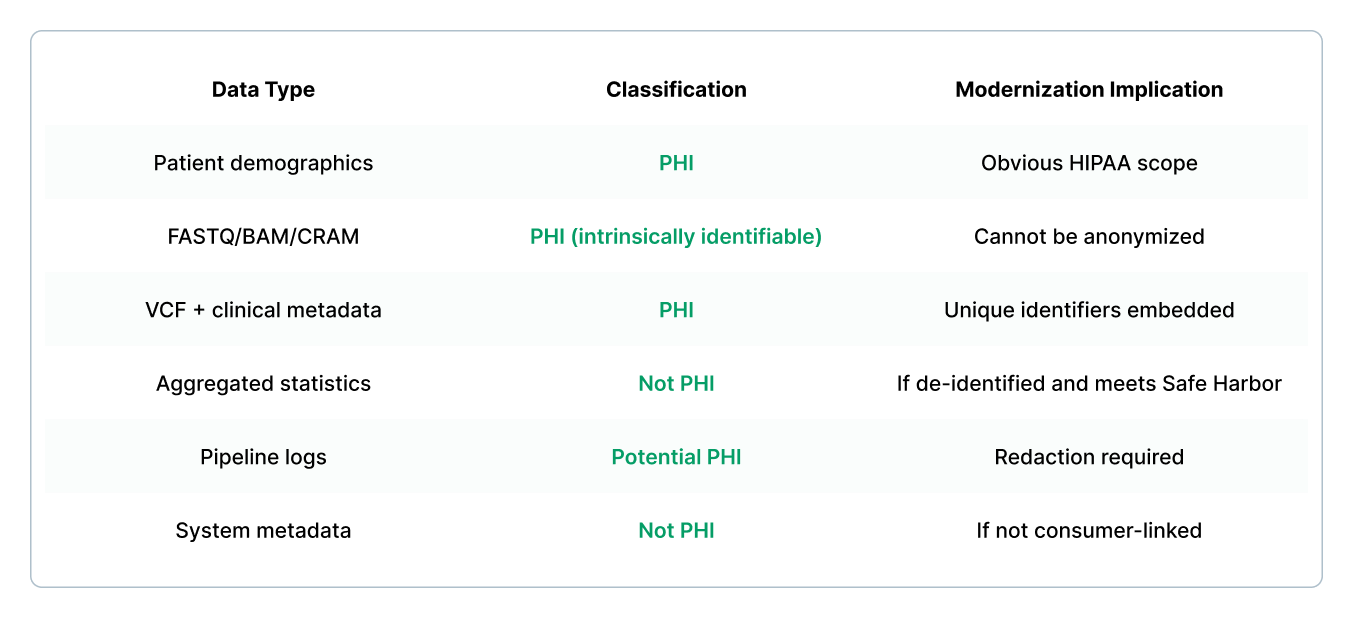
This classification drives the architectural boundary.
Step 2: Architect the PHI Processing Zone
Below is a typical PHI-safe cloud architecture:

Step 3: Secure the Genome Processing Pipeline End-to-End
Pipeline orchestration (Airflow, Nextflow, Cromwell) is often a hidden compliance risk.
Checklist for HIPAA-aligned workflow systems
- No PHI in environment variables
- No PHI in task names or step identifiers
- Log redaction middleware
- Pipeline versioning + reproducible containers
- Pipeline results encrypted in transit + at rest
- Use of short-lived credentials for cloud object access
- Segregated storage for raw vs. interpreted genomic data

Step 4: Implement PHI-Aware Logging and Observability
One of the most common HIPAA violations in genomics platforms is the leakage of PHI from logs.
Sensitive leakage sources:
- Sample IDs passed as CLI args
- FASTQ filenames
- Variant annotations referencing subject IDs
- EHR order IDs
Best practices:
- Use log-scrubbing middleware (regex-based sanitization)
- Maintain PHI sets with known sensitive tokens
- Enforce a strict no-PHI logging policy in code review
- Run logs through DLP (Data Loss Prevention) scanners
Step 5: Establish Identity, Access Management, and Boundary Control
Required IAM principles for HIPAA-ready genomics platforms
- Least privilege: restrict by workflow, pipeline, and role
- RBAC + ABAC hybrid: role + sample/cohort-based access
- No persistent credentials
- Just-in-time elevated access
- Federated SSO (SAML/OIDC)
Boundary controls
- No direct database access
- No cross-region PHI replication unless strictly required
- Egress restriction for PHI zones
- Use VPC endpoints for storage access
Step 6: Build a Fully Auditable Data Lineage System
Clinical genomics pipelines require complete traceability.
HIPAA doesn’t explicitly require lineage, but CLIA and CAP expectations make it essential.
What an adequate lineage system captures
- Source FASTQ checksum
- Software versions for alignment and variant calling
- Reference genome version
- Filter parameters
- Interpretation model version
- Timestamped operator actions
- EHR order linkage
A modern lineage system is typically stored as structured metadata in a non-PHI store, linked by a hashed identifier.
Step 7: Prepare for EHR and LIMS Interoperability
Interoperability adds both value and compliance burden.
Required safeguards when integrating with EHR systems
- FHIR server with strict authentication
- Audit trails for every FHIR resource read/write
- Controlled vocabularies (LOINC, HGVS, ClinVar)
- PHI sanitization for outbound variant annotations
- Queue-based message passing to avoid direct coupling
Required safeguards for LIMS connectivity
- API gateway enforcing request-level auth
- Versioned schema contracts
- Full observability for cross-system data flow
- Structured error objects, no PHI in error messages
Step 8: Validate Against HIPAA Technical Safeguards
A minimal compliance checklist:

Step 9: Conduct a HIPAA Security Risk Assessment (SRA)
The required HIPAA SRA should:
- Enumerate all data flows
- Identify PHI touchpoints
- Evaluate controls against threats
- Document mitigation strategies
- Map storage, compute, and orchestration to risks
Teams that skip SRA inevitably fail compliance audits.
Build vs Buy: What's Actually Practical for Genomics Teams
Below is an objective comparison based on real-world platform builds.

Compliance: Beyond HIPAA - What Genomics Platforms Must Also Address

A genomics platform cannot rely solely on HIPAA for compliance; it must operate under a multi-regulatory umbrella.
Cost & ROI Discussion
A HIPAA-ready genomics platform includes:
Initial CapEx
- Cloud environment configuration
- Secure pipeline orchestration
- EHR/FHIR gateway
- Audit log infrastructure
- IAM + RBAC design
- Compliance architecture review
For most mid-sized genomics organizations, the largest costs are security engineering + pipeline productionization, not sequencing compute.
Ongoing OpEx
- Security patching
- Business continuity
- Penetration testing
- Access reviews
- Pipeline container maintenance
- Observability stack cost
ROI Sources
- Faster onboarding of new assays
- Reduced compliance-risk overhead
- Faster integration with clinical partners
- Efficient computing from optimized pipelines
- Reproducibility → lower QC overhead
- Automated reporting → higher throughput
Teams often see major ROI once pipeline failures decrease and clinical turnaround times shrink.
Common Mistakes We See in HIPAA-Focused Genomics Builds
- Putting PHI in SQS/Kafka messages: Always pass references, never identifiers.
- Using the same bucket for raw + processed genomic data: Segregation is essential for lifecycle controls.
- Logging sample IDs accidentally: Especially in workflow orchestrators.
- Developers having direct access to production VPC: This is a guaranteed audit failure.
- No deletion automation: Genomics data accumulates explosively.
- Pipelines not version-pinned: Invalidates lineage and CLIA expectations.
- Treating compliance as a security project instead of a product requirement
Compliance is a product capability.
Best Practices for HIPAA-Ready Genomics Development
Architectural
- Isolate PHI-heavy workloads in dedicated zones
- Use infrastructure-as-code for reproducibility
- Enforce short-lived compute credentials
Pipeline
- Immutable containers
- Automated quality gates
- Zero-PHI logging policy
Data
- Classification and tagging
- Tiered storage with retention rules
- De-identification pipelines for R&D
Ops
- Quarterly tabletop incident response exercises
- Rotating penetration tests
- Vendor access monitoring
- Continuous compliance monitoring
Team Practices
- Cross-functional collaboration: bioinformatics × security × software
- Documented SLIs/SLOs for pipelines
- Access reviews tied to HR processes
Why Leading Genomics Teams Work with NonStop for HIPAA-Ready Platform Development
NonStop has spent more than a decade building HIPAA-ready genomics platforms that combine secure cloud architecture, clinical-grade bioinformatics pipelines, and compliant EHR/LIMS integrations. Our engineering teams specialize in secure cloud architectures, PHI-aware data pipelines, and compliant workflow orchestration that meet the technical safeguards required for HIPAA, SOC 2, and CLIA. We help teams architect the full lifecycle of genomic data, ingestion, processing, interpretation, reporting, and EHR/LIMS integration using battle-tested patterns that eliminate common compliance failures such as uncontrolled PHI propagation, non-auditable pipelines, and weak IAM boundaries.
Because we sit at the intersection of bioinformatics, cloud infrastructure, and clinical interoperability, NonStop can identify gaps early, reduce rework, and deliver platforms that are not only compliant on paper but also reliable, scalable, and production-ready for high-throughput genomics and clinical use.
HIPAA-readiness in genomics platforms is rarely about checking boxes. It's about designing platforms that embed data governance, security controls, pipeline reproducibility, and clinical interoperability from the start.
Teams who treat compliance as an engineering capability, not an afterthought, build platforms that scale faster, integrate more reliably, and earn trust across clinicians, labs, and partners.
If your team is exploring modernizing LIMS workflows, building cloud-native genomics tools, or integrating EHR/LIMS systems with AI and built-in compliance, NonStop is always open to a conversation. We've spent over a decade helping genomics and healthcare organizations design, engineer, and scale platforms that last.



%201.jpg)