Securing Digital Products with Proactive DevSecOps
Cloud Security &
DevSecOps
At NonStop, we embed security across the development lifecycle, delivering enterprise-grade cloud and application protection. Integrated into DevOps, we reduce risk, protect critical data, and accelerate digital transformation.


Our Key Security Services
At NonStop, security is embedded across the development lifecycle to protect cloud infrastructure, applications, and data while enabling compliance, resilience, and operational efficiency.

Cloud Security
At NonStop, we deliver cloud security solutions that protect AWS, Azure, and GCP infrastructure through proactive threat management and continuous security controls.
- Implements robust access controls, encryption, and continuous monitoring to secure cloud environments
- Reduces downtime while strengthening infrastructure resilience and ensuring compliance readiness
Application Security
We secure enterprise applications across development and deployment to reduce vulnerabilities and support consistent performance at scale.
- Enforces secure coding practices and continuous vulnerability scanning to minimize application risk
- Applies static and dynamic code analysis and Web Application Firewalls (WAF) to protect applications
- Protects APIs using authentication, encryption, and rate-limiting strategies to ensure secure integration
Security Audits & Assessments
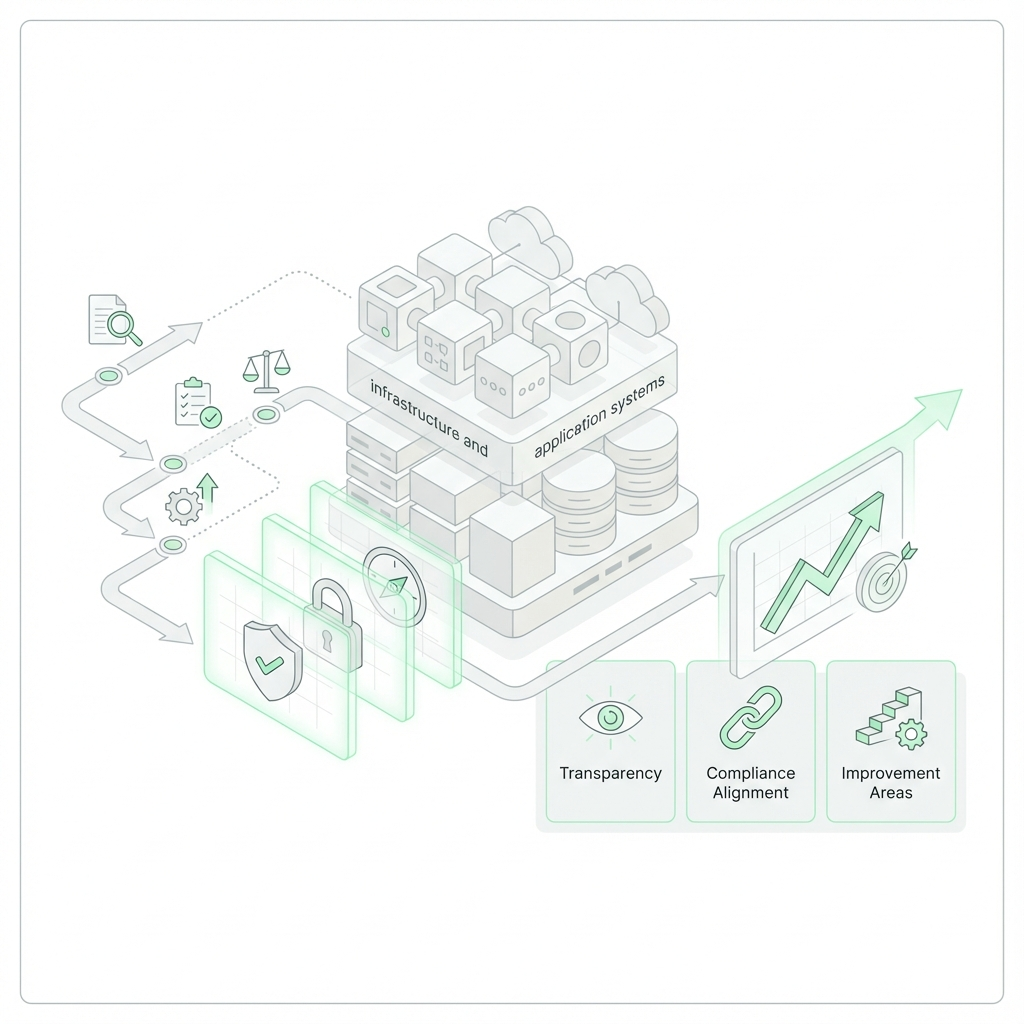
At NonStop, we conduct security audits and assessments to ensure infrastructure and applications remain aligned with regulatory requirements and security best practices.
- Ensures compliance with SOC 2, ISO 27001, and GDPR across systems
- Identifies security gaps and delivers actionable remediation strategies to reduce risk
Risk Management & Mitigation
We help organizations proactively identify, assess, and mitigate security risks to protect mission-critical systems and operations.
- Implements SOC 2-aligned strategies and maintains detailed risk logs
- Enables timely remediation to support continuous protection and operational resilience


Access Control Management
At NonStop, we implement access control management to secure sensitive systems and critical resources.
- Applies Identity and Access Management (IAM) with multi-factor authentication (MFA) and least-privilege access
- Reduces insider threats while ensuring operations remain aligned with compliance standards
Security Monitoring & Logging
We provide continuous security monitoring and logging to improve visibility, detection, and response.
- Uses ELK Stack, AWS CloudTrail, Prometheus, and Grafana for real-time monitoring and logging
- Detects threats early, automates alerts, and minimizes downtime through faster incident response
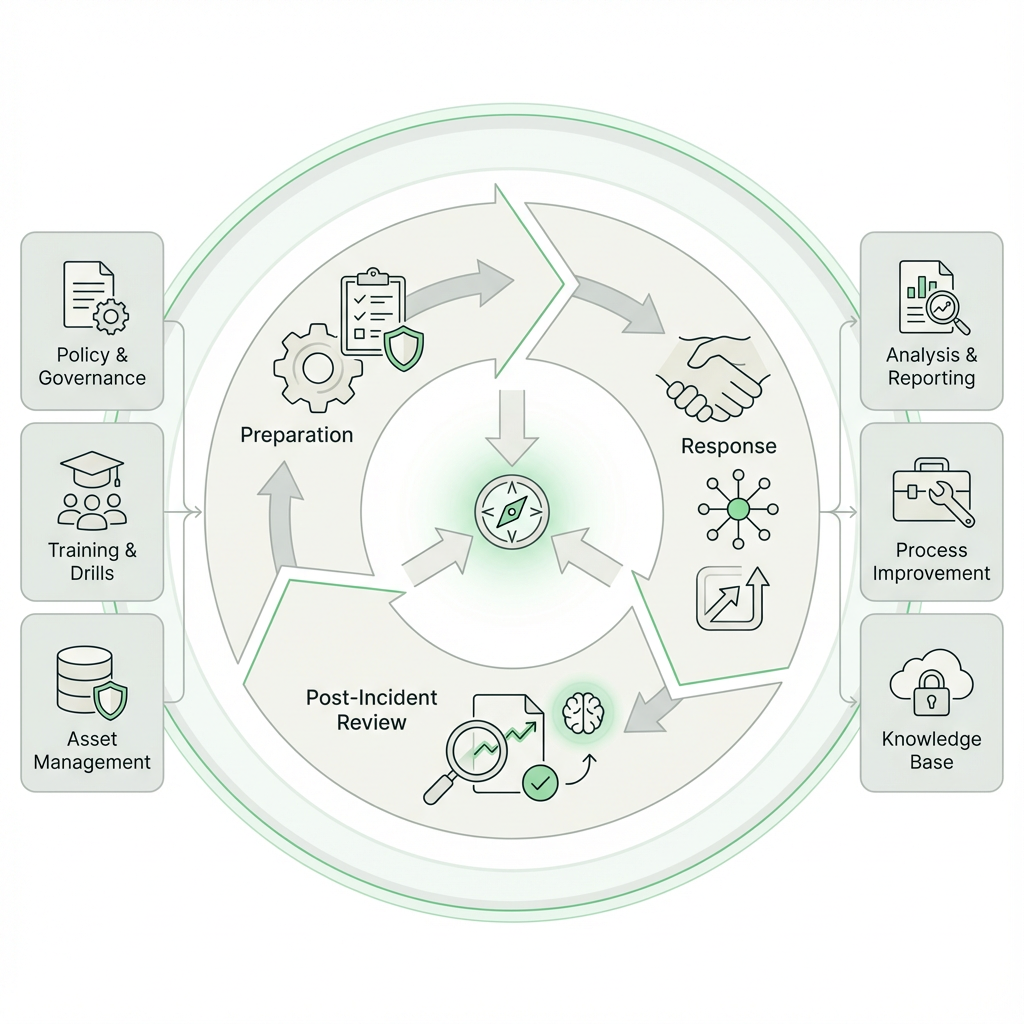
Incident Response Planning
At NonStop, we help organizations prepare for, respond to, and recover from security incidents effectively.
- Creates incident response plans, conducts drills, and performs post-incident reviews
- Supports SOC 2 compliance while enabling rapid mitigation and reduced operational impact
Data Protection
We protect sensitive business data while supporting regulatory compliance and business continuity.
- Encrypts data at rest and in transit to prevent unauthorized access
- Maintains secure backups and retention policies to ensure data availability during disruptions

Business Continuity & High Availability
At NonStop, we design systems that support continuous operations and high availability during disruptions.
- Implements disaster recovery (DR) and business continuity planning (BCP)
- Uses redundancy, failover systems, and high-availability practices to minimize downtime
Compliance Documentation
We simplify audits and compliance processes through complete, audit-ready documentation.
- Maintains policies, procedures, and SOC 2 audit evidence
- Reduces audit effort while ensuring transparency and consistency


Vendor & Third-Party Compliance
At NonStop, we help organizations manage third-party risk across the enterprise ecosystem.
- Assesses vendors for SOC 2 and GDPR compliance
- Reduces third-party risk while maintaining ecosystem security
Our Approach
Security-First Culture
At NonStop, security is embedded at every stage to help teams build resilient infrastructure, reduce risk early,
and maintain continuous compliance through DevSecOps practices.
Continuous Security Testing
Security testing is integrated into the build process to detect vulnerabilities early and protect applications and cloud infrastructure throughout development.
Automated Security Testing
Automated tools and scripts continuously scan and remediate vulnerabilities, reducing human error and accelerating secure software delivery.
Vulnerability Management
Security gaps are proactively identified and remediated to maintain alignment with SOC 2, GDPR, and ISO 27001.
Compliance Automation
Security policies and controls are automated to streamline compliance, simplify audits, and ensure regulatory requirements are met.
Secret Management
Cloud secret management, Vault, and secure storage solutions protect critical information and prevent unauthorized access.
Secure CI/CD Pipeline Integration
Security controls are embedded into CI/CD pipelines to prevent misconfigurations and ensure secure, consistent deployments.
Why Choose NonStop for Security
At NonStop, we deliver comprehensive DevSecOps security from development to production, helping organizations reduce risk early, meet regulatory requirements, and maintain secure, reliable operations.
Proactive Security
Security is embedded early in the development process to prevent vulnerabilities and strengthen application and infrastructure resilience.
Compliance Assurance
Our security approach aligns with SOC 2, ISO 27001, GDPR, and HIPAA, enabling continuous compliance and audit readiness.
Automated Security
Continuous security checks across DevOps pipelines and cloud infrastructure support real-time risk detection, faster remediation, and dependable operations.
Our Team's Certifications








Everything You Need To Build, Scale
and Secure Digital Products
AI & ML
Embed intelligence with predictive and generative AI from RAG workflows to ML pipelines for real outcomes.
UI/UX Design
Design human-centered experiences that improve usability and adoption across digital products.
Data Engineering
Build scalable data pipelines and platforms that turn raw data into reliable insights and AI-ready assets.
Frontend Development
Deliver intuitive, high-performance frontends that balance usability, accessibility, and enterprise-grade speed.
Backend Development
Engineer secure, cloud-native backends that scale from MVPs to enterprise platforms without rework.
Mobile App Development
Build fast, reliable, cross-platform mobile apps designed for scale, performance, and user adoption.
Cloud & DevOps
Speed up delivery with CI/CD automation and scalable cloud infrastructure built for uptime and cost efficiency.
Quality Assurance
Ensure product reliability with automated and manual testing that protects performance, security, and user trust.



.gif)